Sharing this as I thought some people might find it helpful.
I use OPNSense on my home network as well, but this gives me far more freedom to experiment and (possibly) break things.
Proxmox as NAT
Proxmox eth0 interface has an IP address on my physical home network. eth0 is a virtual interface inside Hyper V.
Using NAT to translate the addresses because Hyper V wasn’t playing nice with multiple MAC addresses being used.
The block under eth0 contains all the necessary config on Proxmox to do NAT. It also adds a static route for the entire 10.17.200.0/24 network.
/etc/network/interfaces
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 10.17.20.10/24
gateway 10.17.20.1
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up echo 1 > /proc/sys/net/ipv4/conf/eth0/proxy_arp
post-up iptables -t nat -A POSTROUTING -s 10.17.200.0/30 -o eth0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s 10.17.200.0/30 -o eth0 -j MASQUERADE
post-up ip route add 10.17.200.0/24 via 10.17.200.2 dev vmbr0
pre-down ip route del 10.17.200.0/24 via 10.17.200.2 dev vmbr0
auto vmbr0
iface vmbr0 inet static
address 10.17.200.1/30
bridge-ports none
bridge-stp off
bridge-fd 0
auto vmbr1
iface vmbr1 inet manual
bridge-ports none
bridge-stp off
bridge-fd 0
#DMZ
auto vmbr2
iface vmbr2 inet manual
bridge-ports none
bridge-stp off
bridge-fd 0
#Enclave
auto vmbr3
iface vmbr3 inet manual
bridge-ports none
bridge-stp off
bridge-fd 0
#Security Tools
source /etc/network/interfaces.d/*
The windows host also needs a static route added:
route add -p 10.17.200.0 MASK 255.255.255.0 10.17.20.10
As can be seen in the Proxmox network config, 4 virtual bridges have been created:
- vmbr0 is the bridge between Proxmox and the OPNSense WAN (10.17.200.1/30)
- vmbr1 is the DMZ (10.17.200.32/27)
- vmbr2 is the Secure Enclave (10.17.200.64/27)
- vmbr3 is the Security Tools network (10.17.200.96/27)
OPNsense config
I honestly haven’t went super far with this yet.
Traffic coming into the Enclave interface can only go to either:
- DMZ
- Wazuh server (Wazuh agent reporting)
Traffic coming into the WAN interface and destined for the Enclave is dropped.
Wazuh
This is where things got super interesting! I’m currently taking a CIS Controls course (SEC566/GCCC), and it was very helpful to see how many of the controls can be put into practice with the help of Wazuh or other EDR type solutions.
I’m running Wazuh inside Podman containers. The only change needed to the Docker Compose file was adding “:z” or “:Z” to the end of the volume mounts, depending on whether needed in one container or more. This fixes the SELinux security context, BTW, something useful I learned while studying for RHCSA! The plan is to keep SELinux enabled and enforcing, and never run containers as root unless absolutely necessary.
As of the time of writing, RHEL 10 is not fully supported, so don’t make the same mistake I did… verify your distro is supported before building.
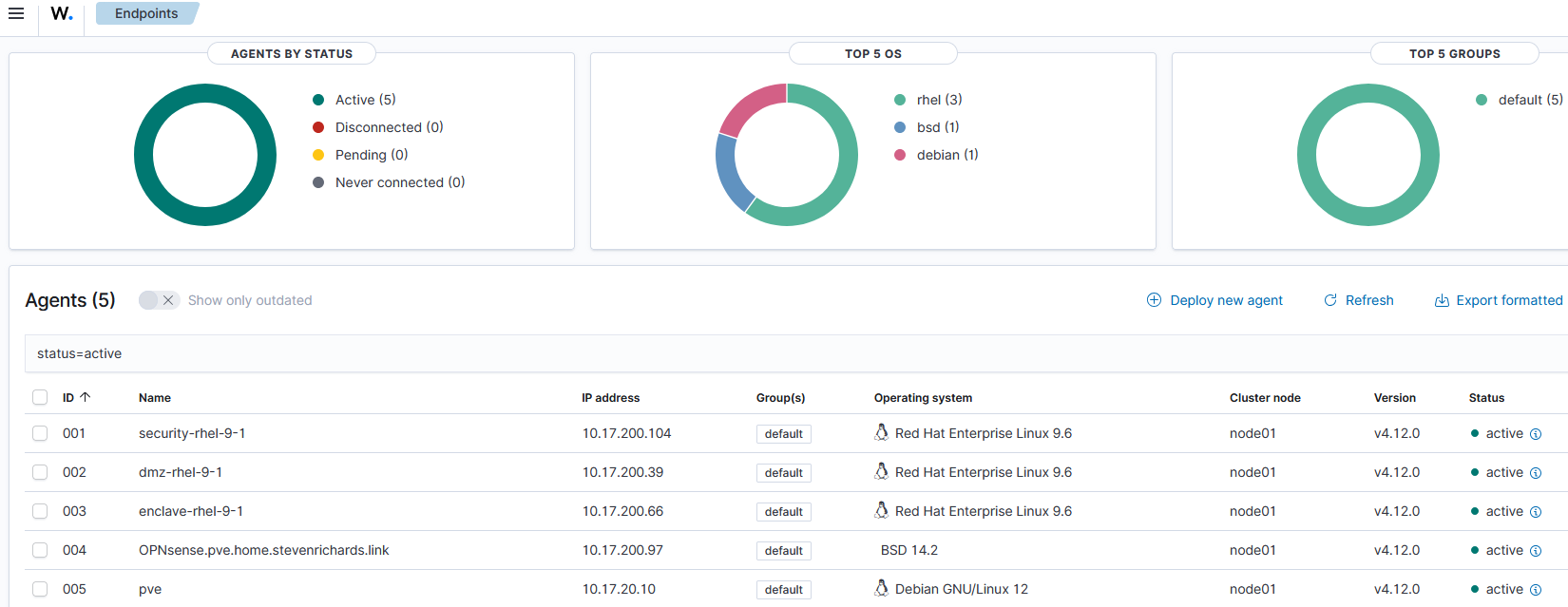
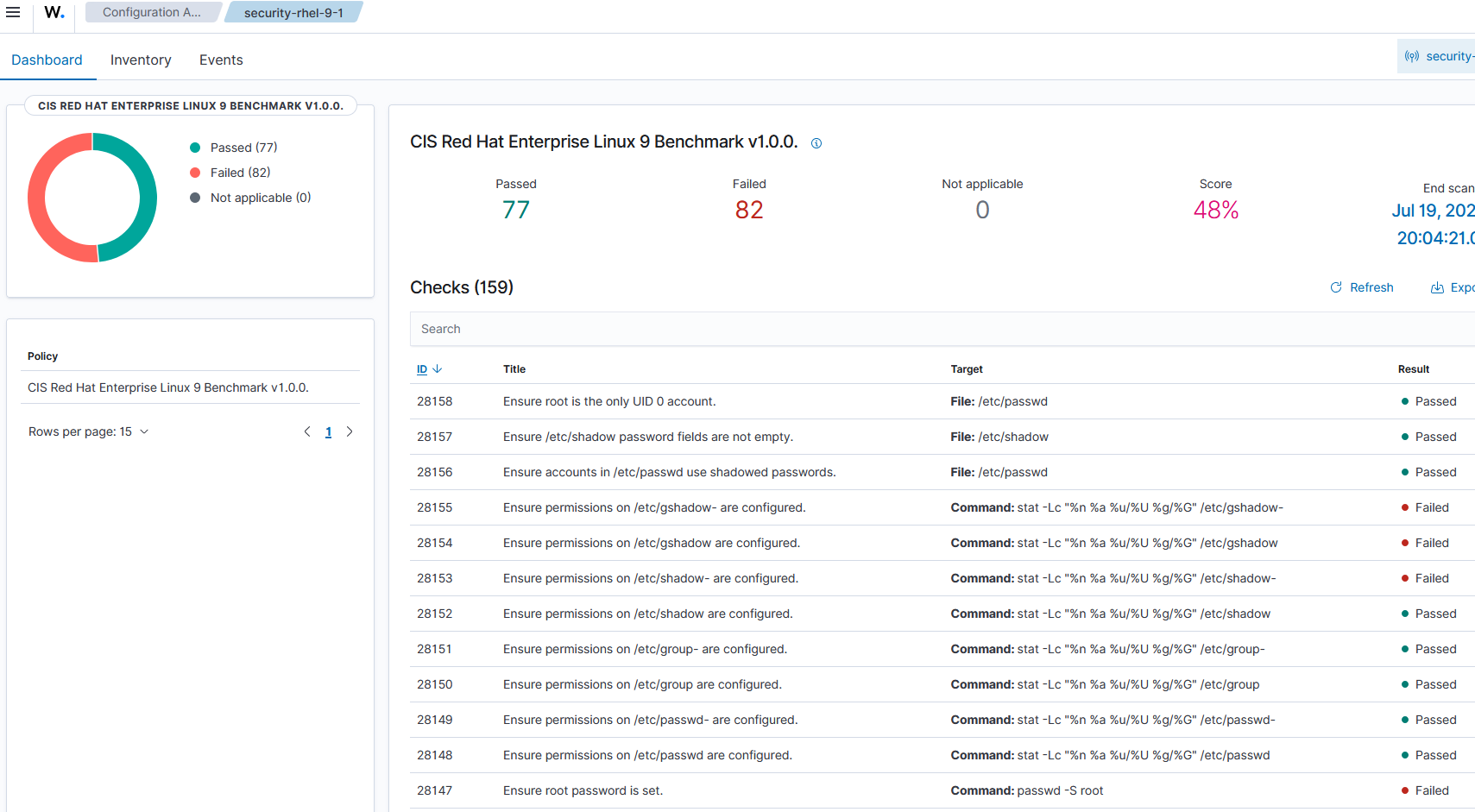
Configuration Assessment against CIS Controls
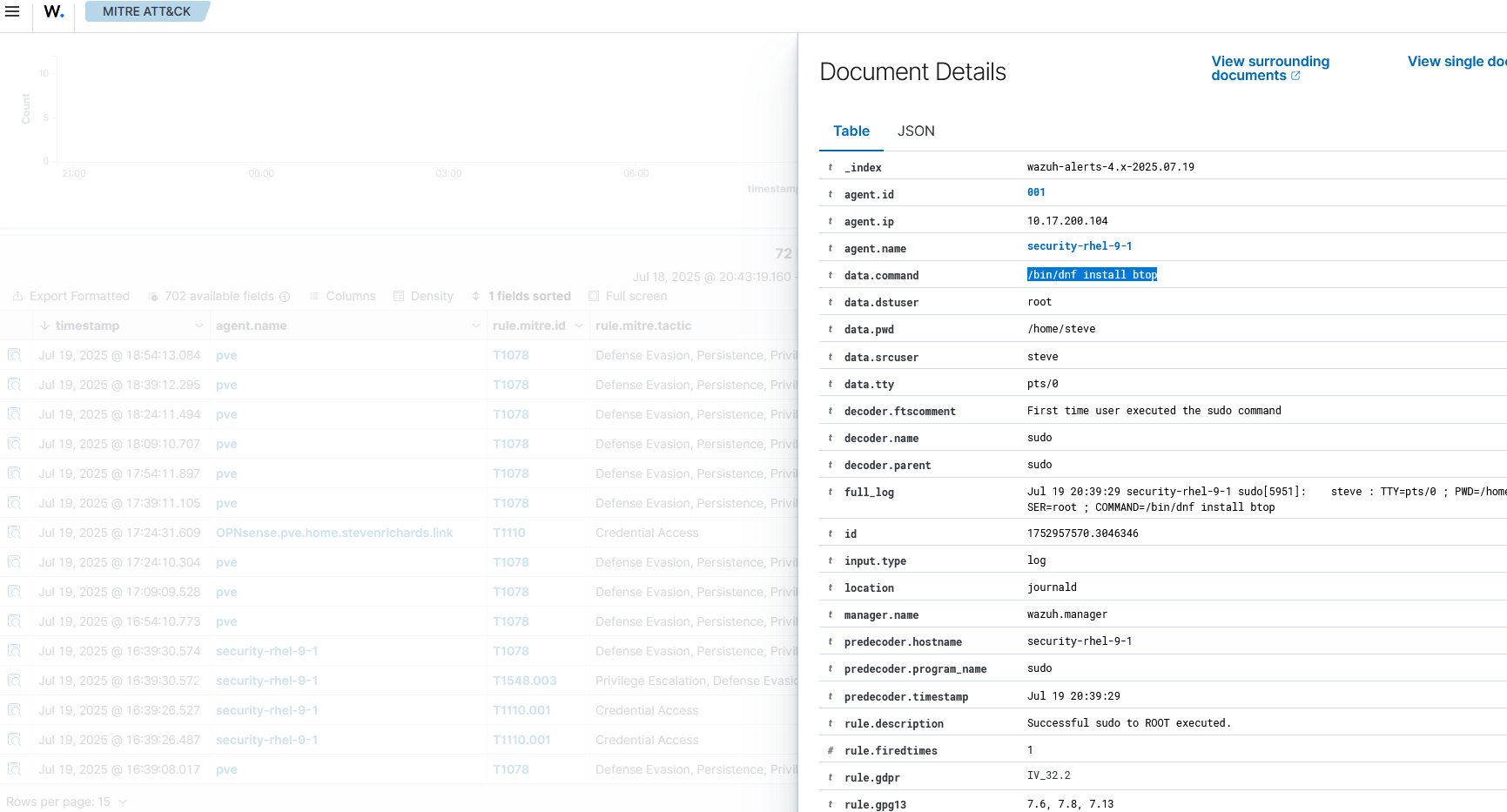
Command History
There’s a lot of work left to do! This is just the start. Now to learn to sift through this data, apply the CIS recommendations if they fit my needs, and find some more fun tools to play with!